What is SHA-1?
SHA-1 is a weak but still widely used hash function that takes an input and converts it to a Hash Value also called a message digest, which is practically impossible to reverse. when we feed a message to this hash function, it will produce a 160-bit hash value known as a message digest.
SHA-1 and its other variants are usually used to check the integrity of the file or whatever data we are sharing over an unsecured and/or secured medium. for example, if we are transmitting a file from person A to person B, SHA can help us to check if the file is intact and has not been altered. This can be checked if both the checksums are identical.
Where do we use SHA?
- Digital Signature:
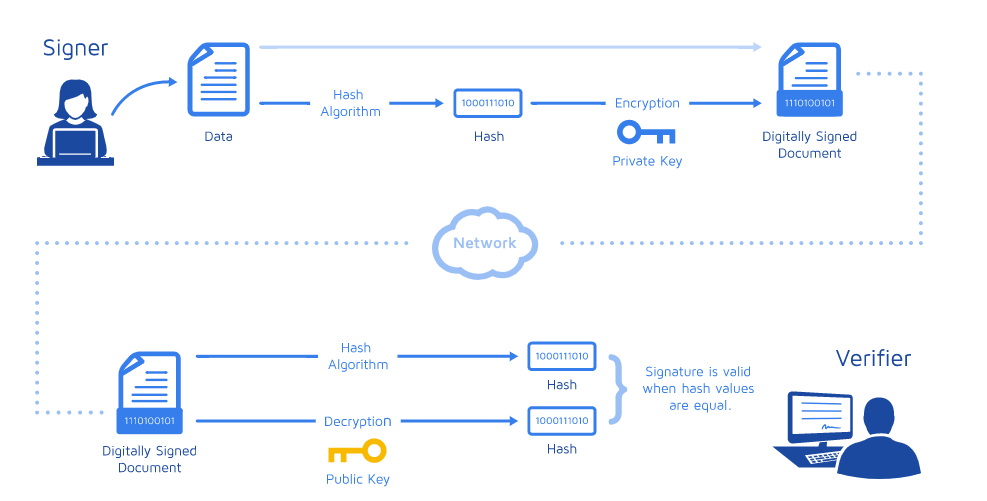
One special use case is the digital signature. It can be used in the signing and verification process of the digital signature.
In a digital signature, we hash the data or doc first and then apply the encryption on the hashed data, which is called a digitally signed document. At the verification end, the verifier applies the hash algorithm on that digitally signed doc to generate the hash value and eventually decrypts the data. A signature is considered valid when hash values are equal.
- Hashing the Passwords inside the Database:
Imagine you are logging into any website and it is responding that your password is incorrect. This is due to the reason that your password doesn’t match the password stored in the database. Now to be specific, companies use hash functions to secure your password inside the database, your password string is converted into a hash and stored inside the database.
Once you try to log in by providing your password, a hash, or you can call it a message digest is generated and compared with the stored hash inside the database. If the hash generated is identical to the hash stored, you are allowed to login into that website.
Now, you got an idea why your password was not accepted in the first place.
Why does Oracle Disable it in their latest upgrade?
SHA-1 is considered a weak algorithm and has many vulnerabilities that can impact, vulnerabilities like Freak Attack, HeartBleed, LogJam, etc. We will discuss these vulnerabilities in detail in another post or you can do a quick google search to find what these vulnerabilities are all about.
What is Impacted?
Any Java application that is using jars signed with SHA-1 and signed after 2019. As per Oracle ” any JAR signed with SHA-1 algorithms and timestamped prior to January 01, 2019, will not be restricted”
Workaround:
Step 1: Run “jarsigner -verify -verbose –certs <Jar file name >“ to check if your signed jars are affected by this java upgrade.
Example: jarsigner -verify -verbose -certs IngrianNAE-8.12.6.000.jar, the output may vary depending on which jars you are using.
s = signature was verified
m = entry is listed in manifest
k = at least one certificate was found in keystore
i = at least one certificate was found in identity scope
? = unsigned entry
- Signed by "CN=aadilnabi, OU=Java Software Code Signing, O=Oracle Corporation"
Digest algorithm: SHA-1 (disabled)
Signature algorithm: SHA1withDSA (disabled), 1024-bit key (weak)
Timestamped by "CN=DigiCert Timestamp 2022 - 2, O="DigiCert, Inc.", C=US" on Wed May 04 06:32:34 UTC 2022
Timestamp digest algorithm: SHA-256
Timestamp signature algorithm: SHA256withRSA, 4096-bit key
WARNING: The jar will be treated as unsigned, because it is signed with a weak algorithm that is now disabled by the security property:
jdk.jar.disabledAlgorithms=MD2, MD5, RSA keySize < 1024, DSA keySize < 1024, include jdk.disabled.namedCurves, SHA1 denyAfter 2019-01-01
Step 2: Open java.security file and modify the below 2 fields.
(a): jdk.certpath.disabledAlgorithms
(b): jdk.certpath.disabledAlgorithms
I was not able to find the above fields in the 8u351 release, so I added it manually.Step 3: You can paste the below to the end of the java.security file or you can modify it as per your requirement.
jdk.certpath.disabledAlgorithms=MD2, MD5, SHA1 jdkCA & usage TLSServer,
RSA keySize < 1024, DSA keySize < 1024, EC keySize < 224,
SHA1 usage SignedJAR & denyAfter 2025-01-01
jdk.jar.disabledAlgorithms=MD2, MD5, RSA keySize < 1024,
DSA keySize < 1024, SHA1 denyAfter 2025-01-01
Step 4: Run “jarsigner -verify -verbose –certs <Jar file name >“ to check if your jars are verified and “disabled” is gone. You can see the below output, and it may vary depending on the jar you are verifying
s = signature was verified
m = entry is listed in manifest
k = at least one certificate was found in keystore
i = at least one certificate was found in identity scope
- Signed by "CN=aadilnabi, OU=Java Software Code Signing, O=Oracle Corporation"
Digest algorithm: SHA-1 (weak)
Signature algorithm: SHA1withDSA (weak), 1024-bit key (weak)
Timestamped by "CN=DigiCert Timestamp 2022 - 2, O="DigiCert, Inc.", C=US" on Wed May 04 06:32:34 UTC 2022
Timestamp digest algorithm: SHA-256
Timestamp signature algorithm: SHA256withRSA, 4096-bit key
jar verified.
Warning:
This jar contains entries whose certificate chain is invalid. Reason: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to
requested target
The SHA-1 digest algorithm is considered a security risk. This algorithm will be disabled in a future update.
The SHA1withDSA signature algorithm is considered a security risk. This algorithm will be disabled in a future update.
The DSA signing key has a keysize of 1024 which is considered a security risk. This key size will be disabled in a future update.
The signer certificate will expire on 2025-04-16.
The timestamp will expire on 2033-03-15.
Important Points:
- Any JAR signed with SHA-1 algorithms and timestamped prior to January 01, 2019, will not be restricted
- Users can, at their own risk, remove these restrictions by modifying java.security configuration file
Reference:
Oracle CRN Link https://www.oracle.com/java/technologies/javase/8u351-relnotes.html
JDK Bug Ticket: https://bugs.openjdk.org/browse/JDK-8264362